Hacking The Cybersecurity Market – A Blume Report
- Published
- Reading Time
- 5 minutes
As per GDPR, the penalties in case of a data breach can be up to €20 million or 4% of the company’s global annual turnover (of the previous financial year), whichever is higher. A data breach could lead to several below the surface losses for an enterprise in addition to the evident ones. This might make us think that data breaches (& other cyberattacks) are not all that common! But on the contrary, a simple Google search would throw up tens of pages of recent news and breach announcements. And the scariest thing is that these are just a (small) part of the incidents which were identified and reported. According to a recent IBM study, an average data breach cost a total of $3.92M with a cost per lost record of up to $150. The data breach of 2017 cost at least $575M to Equifax!!
Resource
- The full report can be found here. PowerPoint
We can’t reemphasize the business impact a cyber attack can have and the magnitude of impact that a missing layer (solution) from the security blanket can cause.
We at Blume therefore decided to develop some level of understanding of the vast cybersecurity universe and make some sense of the solutions available in this complex threat environment. In the process, we developed a detailed report that helped us understand topics ranging all the way from a typical firewall to Quantum Random Number Generators and QKD! (seemingly basic concepts to experts but Greek to us just a month back).
The first challenge that we faced was how to categorize the hundreds of solutions that exist in the market while ensuring that the classification framework works with the new categories that are emerging and expected to see adoption shortly. The traditional approach is that of the security perimeter and castle-and-moat concept of cybersecurity. But we took a different approach as the network perimeter itself is dissolving as we speak!
We’ve divided the entire universe of cybersecurity into three broad buckets namely:
- Protection stack
- Security operations
- Security Culture and Governance
More and more endpoints exist outside the enterprise perimeter and sensitive data & applications are being accessed remotely on unmanaged devices. NIST’s IPDRR that talks about the five core functions of cybersecurity are comprehensive in a way but this isn’t intuitive to folks like us who start with zero domain experience. The majority of current cybersecurity market share is that of Security Services like VAPT, etc.
From the Indian ecosystem POV close to 30-40% of the startups are service focussed, driven by the labour arbitrage in the IT/ITES market.
Under each of the broad buckets mentioned in the slide, the solutions can be hardware-based products, software products that can be deployed on-prem or cloud-delivered, or both and security services. We have added a definition of how we look at different categories in the public version of our cybersecurity investment report. Each of the broad categories has multiple other sub-categories (like Network Security) which in turn have the different solutions under them (like NGFW). We need to understand and accept the fact that here the demarcation is very blurred and the categories in our definition cannot be MECE!
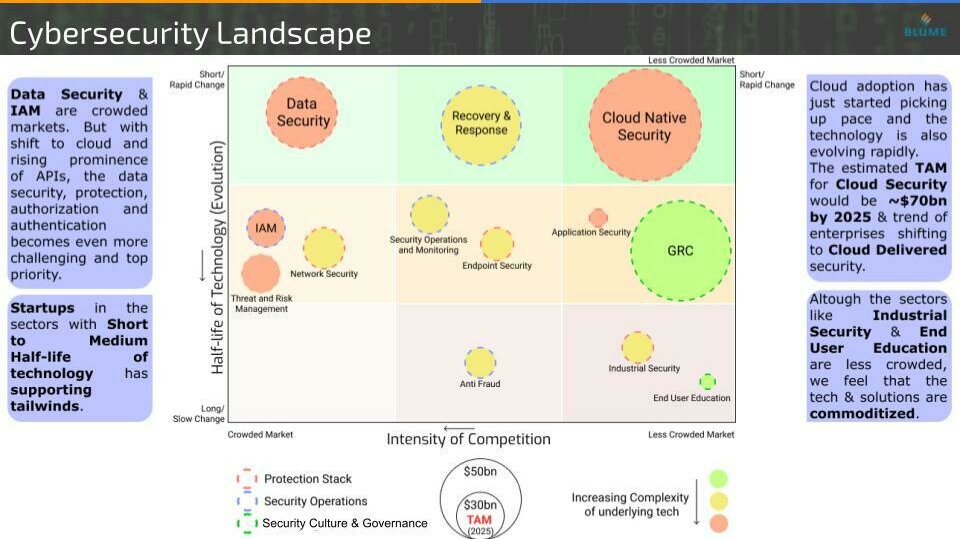
Evaluating a space as vast as cybersecurity could be overwhelming and confusing. We needed a framework to guide us in the process while allowing us to take a sneak peek at the future potential of different solution categories. We do this by mapping across what we consider as the two most important variables the half-life of technology and the market concentration.
If in a particular solution category, the tech is changing rapidly i.e. a shorter half-life of technology, it might outpace the capacity of a company to innovate. In that case, there might be a lot of new players emerging in the respective domain. A lot of niche players emerge and dominate such a category. Now the beautiful thing about cybersecurity is that the whole market of ~$300 bn has over 100+ such categories each with a multi-billion dollar market potential – tens of unicorns!!
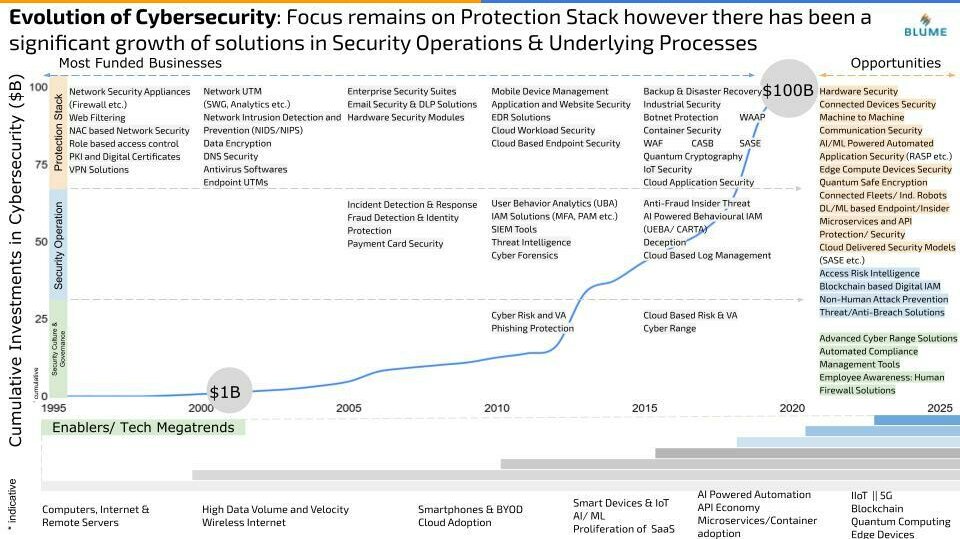
Now that we have a broad classification of the cybersecurity landscape and a framework in place to map different categories, it is important for us to understand the evolution of the space and different tech megatrends that have shaped it. Cybersecurity as an industry has come a long way and has seen rapid growth in the last 2 decades or so. From $1 Bn of total investment in the space in around 2001 to almost $100 bn in 2020 (and this is just going to go up from here – Tracxn). Although the funding is not the best metric of growth, it surely is a positive signal and narrates the journey of the industry to a certain extent.
The focus initially was around securing the core infrastructure and digital assets and hence the different solutions in the protection stack were gaining vital traction. Slowly as the cyber exploits became more frequent and common, the solutions categories to cope with them and fight any attempt of exploit grew. But strengthening the weakest links of any enterprise security infrastructure – employees / humans – has been a persistent challenge for organizations. They all aim to build human firewalls via training and user education. Additionally, with the stringent policies and more compliance to meet, Governance and Risk Compliance solutions and services became important too.
We realized that each of these waves of evolution was enabled by few tech megatrends and it is imperative to envision how the emerging technologies of today can shape the security needs and solutions for the next wave of evolution.
Some of the opportunities that we could map out include:
Protection Stack
- DL/ML based Endpoint/Insider Protection
- Microservices and API Protection/ Security
- Unified Security delivered via Cloud (SASE etc.)
- Connected Devices Security
- Machine to Machine Communication Security
Security Operations
- Access Risk Intelligence
- Non-Human Attack Prevention
- Threat/Anti-Breach Solutions
- Blockchain-based Digital IAM
Security Culture and Governance
- Employee Awareness: Human Firewall Solutions
- Advanced Cyber Range Solutions
- Automated Compliance Management Tools
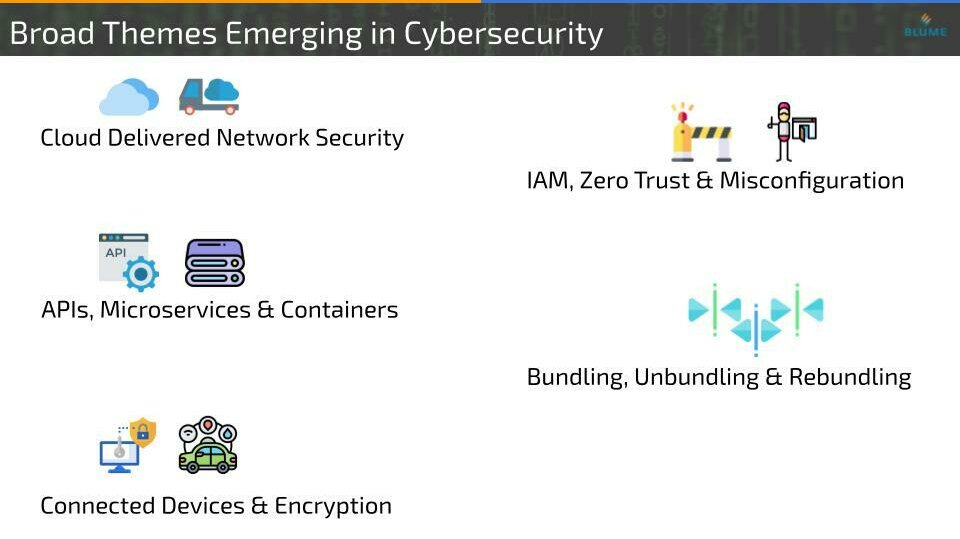
With our analysis and multiple conversations with the industry experts, some of the themes became evident to us. Cloud delivered security, Zero Trust, Protection for the Microservices, and APIs to name a few. One more theme in the evolution of cybersecurity we found interesting was the unbundling of security solutions and services and the re-bundling that is happening now. Network UTMs, Endpoint UTMs, and Enterprise Security Suites started appearing in the late 1990s which were bundled solutions to cater to the security demands of an enterprise or their digital assets. Over the years the complexity of threats was increasing rapidly and vulnerabilities were rising in the applications and enterprise infrastructure. This led to the need for advanced security solutions that can provide specialized security against certain types of threats/vulnerabilities. Payment security solutions, WAF, etc are the individual security products that enterprises deploy on top of the existing security blanket. There was clear unbundling happening in the cybersecurity space.
Now with the emerging themes like SASE and approaches like CARTA, the different advanced solutions are coming together where enterprises can buy/subscribe to a single solution which is highly customizable as per the requirements and is delivered by a single provider. This has led to re-bundling which in our opinion is a theme to stay for the next few years. The higher misconfigurations, remote access, and intelligent non-human attacks which all require a unified solution to counter the threats in the best way while avoiding tens of dashboards, workflows, teams, etc. are some of the core driving factors.
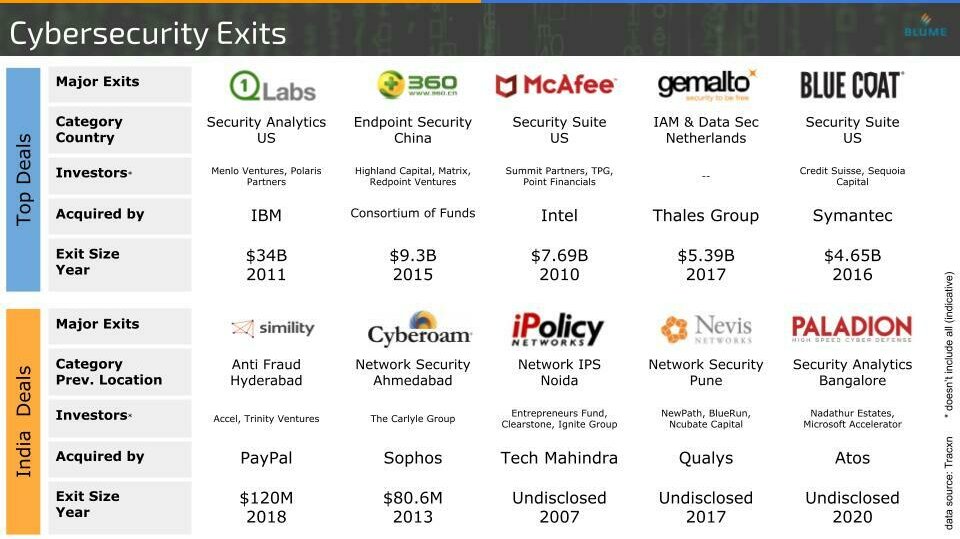
India has some significant exits in the cybersecurity space – with the most recent deals being Paladion getting acquired by Atos and Simility acquired by PayPal. Here we are talking about the space which has seen deals of size up to $34 billion (Q1 Labs acquired by IBM in 2011). The industry clearly is acquisitive in nature and there are ~150 public companies all wanting to broaden their horizon and keeping up their pace with the constant rapid technological evolution.
Talking about and fitting in the Quantum Cybersecurity here won’t do justice to the huge shift that has already started happening around the world. India is also playing its role in this with multiple companies and research labs that are building Quantum Random Number Generators and attempting to solve existing challenges and make Quantum Key Distribution more accessible to enterprises. In our report, we have covered the threat that the upswing of Quantum Computing poses to modern cybersecurity and the challenges for post-Quantum Cybersecurity very briefly.
In the end, we would also like to highlight a rather interesting angle to cybersecurity. Israel is the leading source of innovation in the cybersecurity space (among many other deep tech spaces). Several multi-billion dollar cybersecurity companies have been constantly emerging out of Israel. We performed a comparative analysis of funding trends in technology companies across the US, India, and Israel. As much as 12.8% of total tech investments in Israel have been in cybersecurity companies. This stands at 5.1% and 1.3% for the US and India markets respectively. Another signal! We were curious as to why almost everything great in cybersecurity links back to Tel Aviv and Israel and threw this question to multiple Israel based founders that we spoke with. All resonated with what Dan Senor mentions in his famous 2009 book titled ‘Start-up Nation’ where he says “in this country [Israel], there’s an unwritten social contract: we are going to serve in this army provided the government and the army are responsible towards us….”. The innovation that has been coming out of Israel in Cybersecurity links back to the Military and Mossad! While knowing this fact doesn’t change a lot of things for Blume as a VC firm but definitely gives us certain confidence that we were able to trace back the source of innovation and novelty at least partially while we weren’t actively scouting for it.